In addition to offering better security than anonymous authentication, DCOM authentication offers more flexibility. This is because it lets you specify which users can access your applications. A lot of people are increasingly embracing remote software so it is recommended to stay secure at all times.
What is DCOM authentication level?
The DCOM (Distributed Component Object Model) is a protocol for remote method invocation. It is a Microsoft technology that allows software to be called remotely. The DCOM authentication level controls how much information DCOM provides about itself when it attempts to connect to another application and is based on COM. COM is an object-oriented programming standard that was developed by Microsoft to allow applications written in one language (for example C++) to be used by applications written in other languages. A COM object can be used by any application supporting the standard, provided that it implements the required interfaces. This approach makes it easier to reuse code and share data between applications and software components. In general, DCOM is a technology that enables remote procedure calls (RPCs) between clients and servers. It provides a mechanism for applications to communicate across the network without having to expose their internal data structures and functions to other applications.
Why should I enable DCOM?
Some of the benefits of enabling DCOM include: SPONSORED
Communication between applications – It is possible for different computers or networks to communicate using DCOM. Troubleshooting – Enabling DCOM can help you troubleshoot issues with applications such as Microsoft Exchange Server. Manage and control – DCOM allows you to remotely administer software and hardware on your computer from another computer. It’s almost similar to remote desktop protocols. You can also use DCOM to access information about the capabilities of your computer and its performance.
While DCOM has immense benefits, unfortunately, it also has its downsides. These include:
Excessive control – When you enable DCOM, you allow other programs to control your computer. This means that they can send commands to execute programs on your computer, change the Registry settings, and access other files. Security issues – DCOM can be used by hackers to gain access to your computer. The security risks are high as anyone with malicious intent can take control of your PC. Loss of privacy – If one of the applications on your computer has been infected with a virus or malware, then it can easily steal passwords and sensitive information from other applications on your computer. Slow performance – DCOM requires more system resources than normal applications do and this can interfere with their performance as well as yours. Limited programs – You may be unable to install certain programs. Some software companies do not support DCOM because of security concerns.
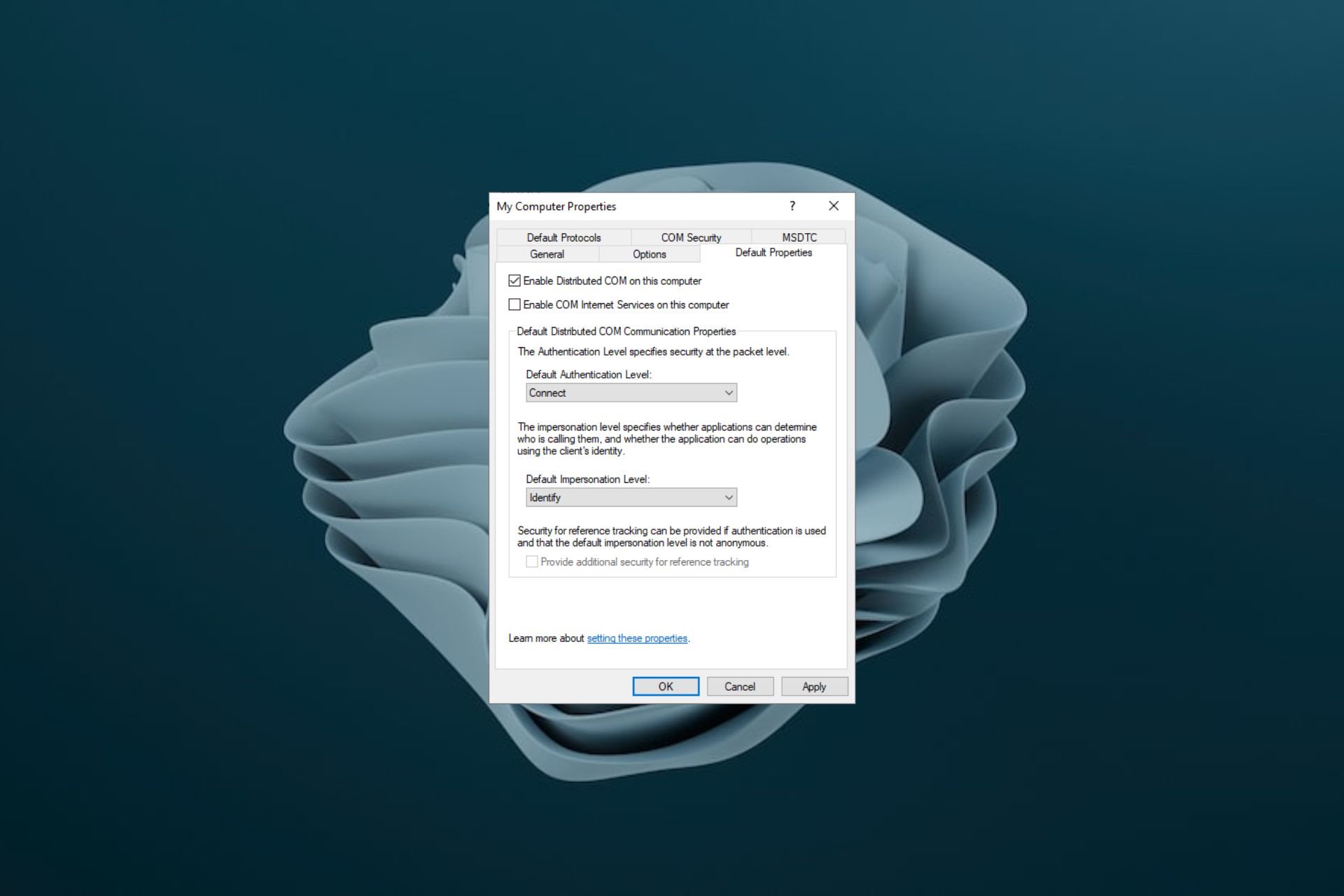
How can I raise the DCOM authentication level?
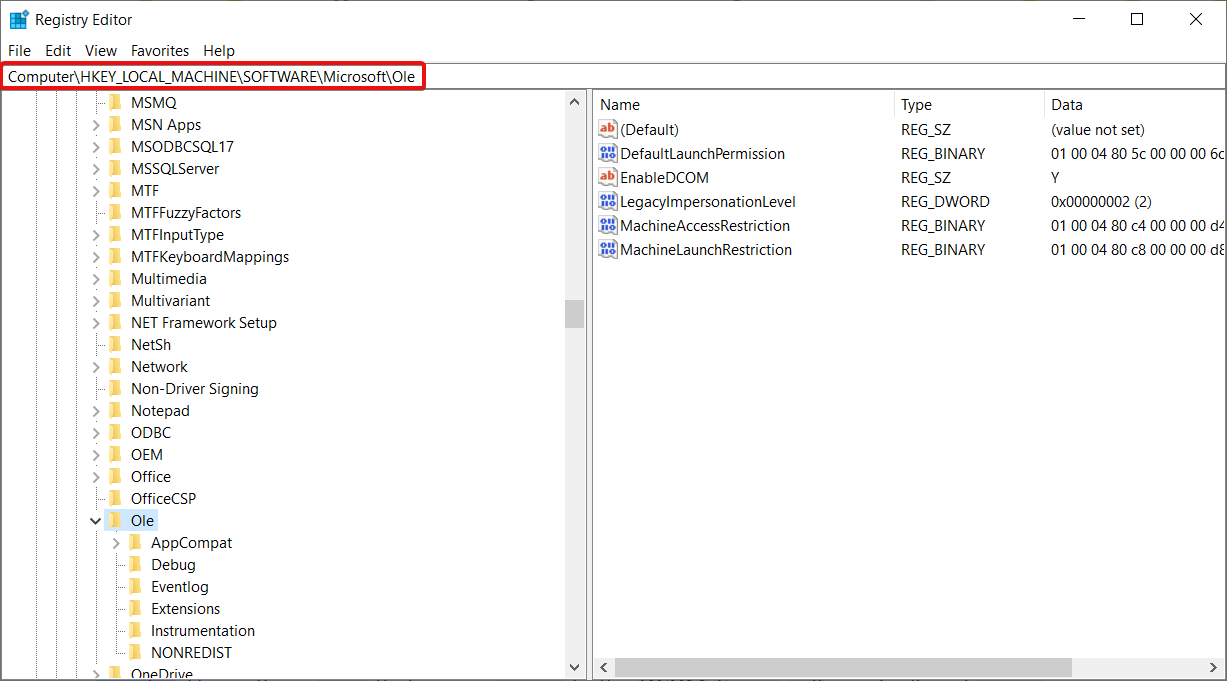
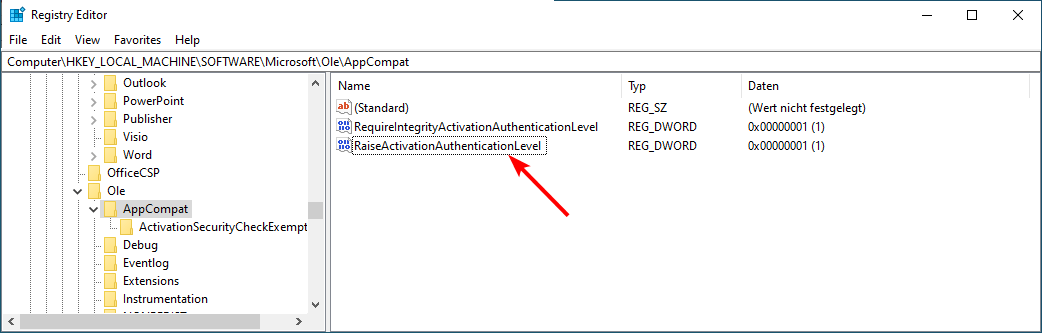
If you get a message such as The server-side authentication level policy does not allow the user %1%2 SID (%3) from address %4 to activate DCOM server. It means that you need to raise your DCOM activation authentication level. Also, you can only edit the registry if you have the KB5004442 Windows update.
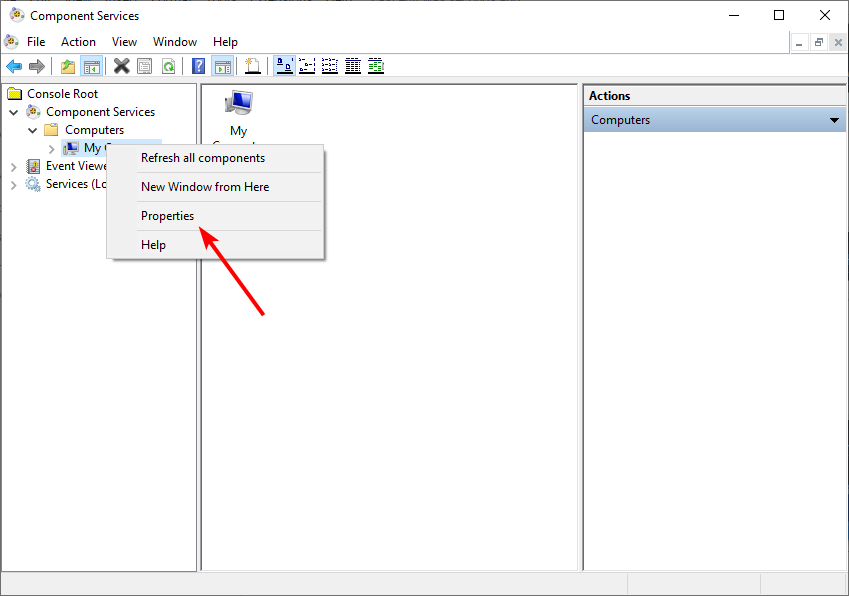
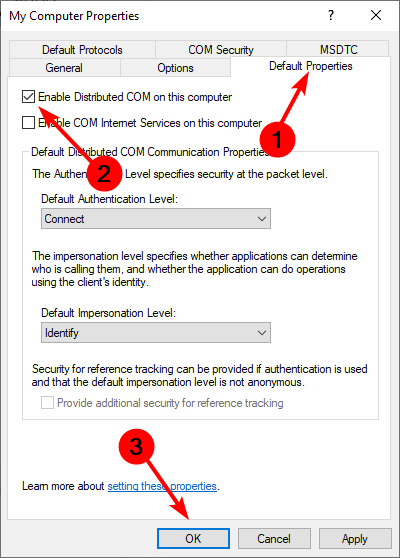
How do I check if DCOM is enabled?
DCOM can be enabled by default on some systems, but it can also be disabled by default or manually. To check whether DCOM is enabled, follow the steps below. By enabling DCOM you expose your system to security vulnerabilities. This can allow attackers to remotely execute code on your computer. If you are not using the protocol, it is best to disable it. For more information on how to manage the DCOM changes, refer to Microsoft’s page. You may also run into a DCOM error 10016 so be sure to check out our guide on how to bypass this issue. We’d love to know what authentication level you have applied if you have enabled DCOM and why. Share in the comment section below.
SPONSORED
Name *
Email *
Commenting as . Not you?
Save information for future comments
Comment
Δ




![]()